Insider Threat refers to a malicious threat to an organization from people within the organization,such as employees, former employees, contractors, or business associates, who have insider information concerning the organization’s security practices, data, and computer systems.
Today, the leading Security Information and Event Management (SIEM) tools collect various data elements based on the static rule set and perform data analysis of user access, machine login, network traffic, and system data. With the rise in the on-demand cloud infrastructure, API- based systems, tools, utilities generate tens and hundreds of events in a single day, making analysis based on static rules obsolete.
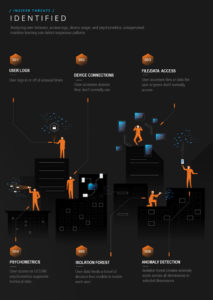
A new approach to insider threat in big data must account for complex human behavior within the monitored environment. Insider threats are, after all, about the actions of humans and not machines, and detection techniques will inevitably incorporate methods from the social sciences.
Core-CSI Insider Threat Detection leverages detecting insider threats with 1) Isolation Forests and 2) Social Network Analysis. In addition to the proposed methodologies, the project also considers unique challenges in the domain, open research problems, limitations, and future directions.