CORE-CSI understands today’s dynamic threats to our customers. Our computer security professionals are well-versed in security best practices mandated by various federal mandates. We follow industry standards and best practices, Department of Defense and Intelligence Community Standards, and National Institute of Standards and Technology to mitigate and defend from Advanced Persistent Threats (APTs).
We provide advanced Computer Network Operations (CNO) and Computer Network Defense (CND), and Information Assurance (IA) services in support of our customers’ missions. CORE-CSI incorporates the NIST-based Risk Management Framework (RMF) to track, prioritize, and mitigate vulnerabilities.
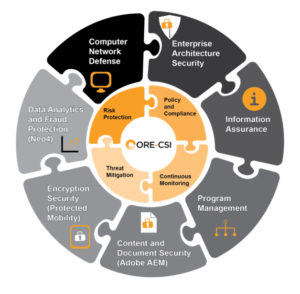
Our cyber security professionals and solutions help secure information, infrastructure, and personnel from threats and attacks to prevent the loss of valuable data and resources. CORE-CSI offers cleared, experienced, certified, and skilled security professionals with expertise across a wide range of programs and information security engineering services.
As one of the world’s leading cybersecurity service providers, we are best placed to help businesses identify, assess, mitigate & respond to the cybersecurity risks they face. We provide our customers with peace of mind that their most valuable assets are protected through an unrivaled suite of services.

